Significant cybersecurity events of the past year.
- Mohnish Singh
- May 24, 2024
- 3 min read
Updated: Oct 6, 2024
The cyber attacks we observed last year have been multi-faceted, be it the emergence of new cybercrime forums, the advent of novel malware and ransomware threats, changing and aggressive tactics of Hacktivism due to shifts in geopolitics dynamics, or state-sponsored cyberwars. Cyber security risks are mounting by the day, and governments and businesses should prepare to confront them in 2024.
Over 7,000 cybercrime forum incidents were reported being actively involved in the sale of
compromised data, unauthorized access, exploits, and multiple claims of data compromises
by financially motivated threat actors and hacktivist groups.Multiple threat groups tried to establish new cybercrime forums in 2023 to capitalize on the opportunity created after the seizure of BreachForums by law enforcement. BreachForums was a popular underground forum for cybercriminals to trade stolen data and coordinate illicit activities before it was taken down.
The closure of BreachForums left a void in the cybercrime ecosystem that other groups sought to fill by launching new forums like BlackForums. BlackForums is a relatively small forum with just over 2,500 members, but it stands out for partnering with the hacktivist group ThreatSec.
Other notable cybercrime forums that remained active in 2023 include:
Exploit - One of the longest-running Russian-language forums, active since at least 2005
the Exploit.in forum homepage screenshot shows an “About” section and different categories for posts about hacking
XSS - A closed forum catering to Russian-speaking cybercriminals, accessible on both the clear web and dark web
The XSS.is forum homepage used by cybercriminals
RAMP - Focuses on ransomware-as-a-service and trading exploits, emerged after other forums banned ransomware discussions
While some new forums emerged, the cybercrime landscape remains dominated by established platforms like Exploit and XSS, which have built reputations over many years. Monitoring these forums is crucial for cybersecurity professionals to detect threats and compromised data early.
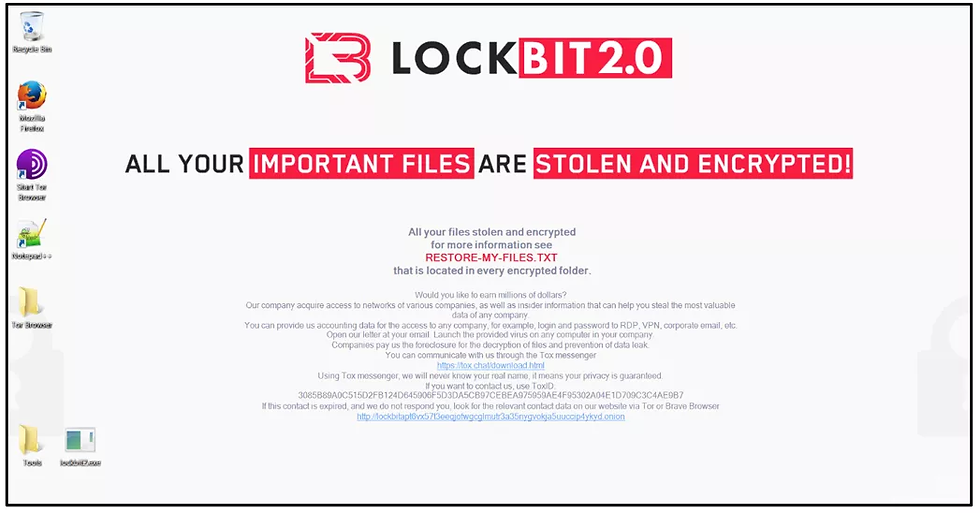
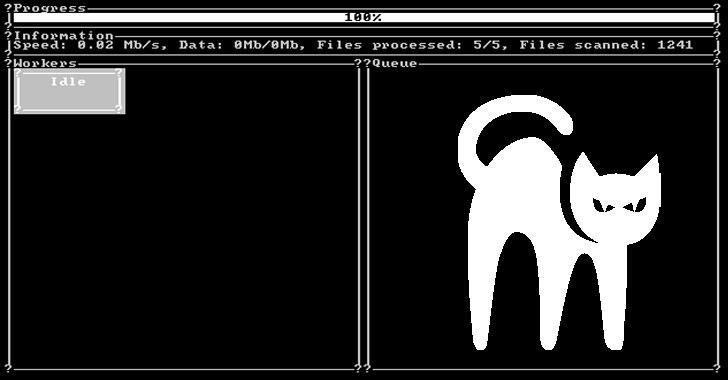
Zero-day exploits targeting - Citrix NetScaler ADC (CVE-2023-4966), PaperCut (CVE-2023-27350), F5 BIG-IP, MOVEit (CVE-2023-34362), Ivanti EPMM, and WinRAR - were observed to be actively weaponized on cybercrime forums as well. Threat actors have increasingly started adopting new languages for malware development, including Rust, Go, and Nim. Ransomware threats doubled in 2023, with disruptions in threat groups and the emergence of new groups and attack vectors. LOCKBIT, ALPHV, and CL0P were responsible for over 42% of ransomware attacks this year.
LOCKBIT:
ALPHV Blackcat :
30+ new ransomware groups emerged in 2023 - well groups include Trigona, NoEscape, Akira,Rhysida,and MedusaLocker.
In 2023, there was a significant increase in the exploitation of Common Vulnerabilities and Exposures (CVEs) by threat actors, who swiftly targeted vulnerabilities of their choice. Malicious actors also continued to exploit vulnerable internet-exposed assets.
Key points from the year include:
Ransomware attacks worldwide were mainly triggered by exploiting vulnerabilities in network devices and Managed File Transfer (MFT) applications.
Analysis revealed a wide range of almost 200 CVEs actively exploited, with notable products from major vendors like Microsoft, Apple, Samsung, Cisco, and Zyxel being targeted.
Out of the 200 vulnerabilities exploited, 30+ were targeted by known attackers, including various ransomware groups.
Threat actors conducted mass exploitation on products from vendors like Progress, Citrix, Apache, and Atlassian.
Ransomware groups such as Cl0P, Bl00dy, and Lockbit3.0 shared a common focus on exploiting MFT applications.
Alongside the proliferation of new forums, the year also saw a surge in the exploitation of vulnerabilities, with threat actors rapidly targeting a wide range of products from major vendors. Ransomware attacks, in particular, were fueled by the exploitation of vulnerabilities in network devices and file transfer applications, underscoring the need for robust patch management and security controls.
As the cyber security risks continue to mount, governments and businesses must remain vigilant and proactive in their efforts to confront these challenges. Strengthening defenses, enhancing threat intelligence, and fostering collaboration across sectors will be crucial in navigating the complex and ever-evolving cyber landscape in the year ahead.


Comments